Prioritizing privacy when it comes to developing IoT services

Ever walked past a surveillance camera in a public space and wondered just how private is your image and data that has been captured? During the January installment of Innov8: A Speaker Series, Dr. Dijiang Huang, Associate Professor of Computer Science and Engineering in ASU’s Ira A. Fulton Schools of Engineering and co-founder of Athena Networks, shared what ASU is doing to prioritize privacy for those on its campuses.

In this discussion on privacy, Internet of Things (IoT) security and cloud computing, Dr. Huang explained how privacy is no longer “just a part of” compliance, legal or auditing. Instead, he urges that privacy needs to be more integrated throughout the organization. “Today, privacy has become very important, especially if we have a lot of IoT devices that have been deployed because those devices can record and monitor the environment, but it also can be used to monitor humans,” said Dr. Huang. “This brings significant privacy concerns.”
Dr. Huang shared the example of ASU’s Smart Campus/City/Region Initiative and how he is working with ASU’s UTO and others to improve the campus IoT systems. One specific project in the works is updating ASU Blue-Light Emergency Boxes on the Tempe campus with sensors and video surveillance to “use the data collected, with respect to privacy and to preserve the digital equity,” said Dr. Huang.
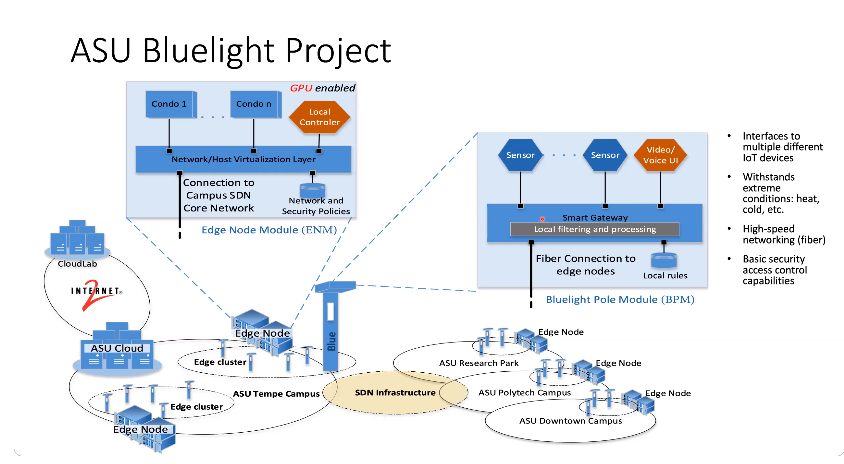
To create a multi-domain IoT Service Architecture needed for the project, Dr. Huang said it’s become popular to create Edge Nodes, which are clusters of computers that act as an end portal user to communicate with others nodes in cluster computing. He walked through design requirements to create such an IoT infrastructure, the importance of Edge Node security and discussed the traffic flow of information within the Node itself.
In the end, Dr. Huang advised that we need to think of privacy as an appliance, a protocol and an infrastructure (or platform) with respect to their impact scope. “When we design this infrastructure, we consider privacy as a main consideration — that’s why we use Edge Computing, memory encryption and distributed deep learning,” said Dr. Huang. “It’s all because we want to achieve a certain level of privacy to protect the data owner and the data model.” Watch the full recording
The next installment of Innov8: A Speaker Series will take place on March 17, 2021 and will cover B2B Process Automation: Using the Public Mainnet as a Common Frame of Reference. Register now!